Identify Risky Access Behavior
Gain visibility and insight into what's normal and what’s atypical behavior as users and devices access your organization’s environment. Duo Trust Monitor delivers advanced anomaly detection by surfacing unusual access and device registration attempts, enabling you to detect and remediate compromised accounts proactively, and harden your network’s defenses.

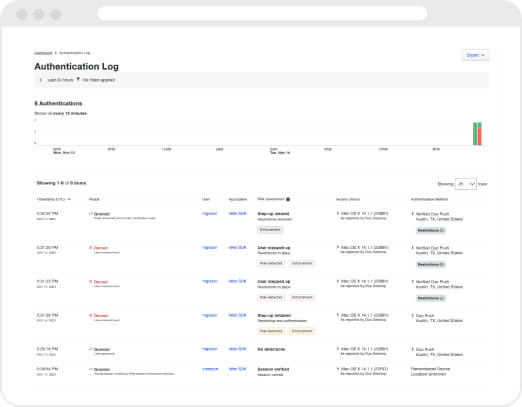
Stop sorting through logs
Sifting through mountains of log data to identify anomalous access events that could be threats to your network is tedious and time-consuming. Trust Monitor gives your security analysts back their time by sorting through your organization’s authentication logs and surfacing unusual access attempts so they can focus on other initiatives.
Set your priorities
Some security events require closer scrutiny. Creating a Risk Profile enables you to prioritize a set of Duo-protected applications, user groups, and locations/IPs. Trust Monitor weights security events involving these priorities as more important than anomalies without a Risk Profile designation and places them at the top of the Security Events dashboard for your attention.
Define your own normal
Decide what “normal” is for your organization. Trust Monitor ingests authentication data, then analyzes and models the data using machine learning to create a baseline of typical user and device access within a corporate environment. Deviations from this baseline can be used to highlight potentially suspicious activity, such as account takeover or application access abuse for fast remediation.
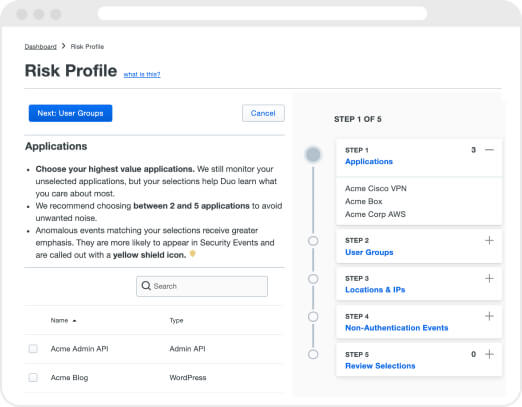
Gain insight through context
Context is key. That’s why unlike risk analytics tools that rely on simple rules, Trust Monitor looks at authentication more holistically and contextually to make sure only truly anomalous activity is highlighted. By including more historical context, more variables, and referencing interactions between variables, Trust Monitor offers much deeper insight into why an access attempt is suspicious.
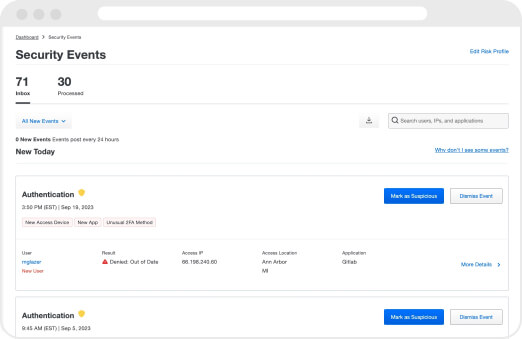
Process anomalous events
When an actionable security event surfaces, Trust Monitor helps you evaluate its threat potential to decide your course of action. You can dismiss the event, mark it as “suspicious” and block the user from future authentications until further action is taken to re-enable the user’s access, or prevent the user from accessing Duo MFA-protected resources, while also removing the session cookies for those resources.
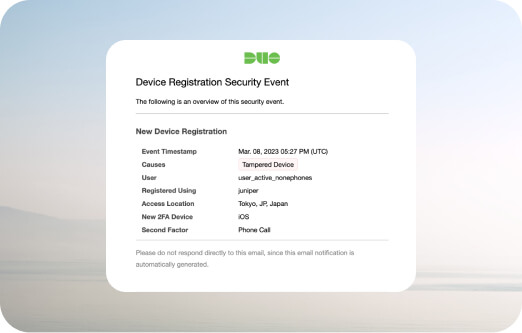
Receive proactive alerts
Staying up to date on potential threats is challenging. Trust Monitor email notifications proactively sends an email each time a new security event surfaces in your environment to help you maintain an awareness of your organization’s security posture without having to log in to the Duo Admin Panel.

Leverage your existing SIEM
Security Information and Event Management (SIEM) tools collect and analyze security event data to add richer context around why an event looks suspicious. Trust Monitor provides the flexibility to export risk events via API to leading SIEM solutions such as Splunk, enabling you to extend and enhance your threat intelligence capabilities.
"Duo Trust Monitor is a detection benefit many MFA solutions don't provide out of the box. For us, the highlighted risky events have been fairly spot on with very few false positives." Read the Customer Story
— Jason Waits, Chief Information Security Officer, CISO, Inductive Automation


